Terraform • HIPAA context
HIPAA‑ready AWS modules for fast, reproducible environments
Composable Terraform modules I use to bootstrap secure, auditable AWS stacks for SaaS and data products. Opinionated defaults for networking, IAM boundaries, logging, encryption, and runtime isolation. Built from field experience operating HIPAA‑regulated workloads.
What you get
- VPC with public/private subnets, flow logs, and egress control.
- ECS (or EKS) application plane with per‑service security groups and task‑level IAM roles.
- ALB + ACM TLS, CloudFront CDN option, Route 53.
- RDS/Aurora with encryption at rest and automated backups.
- Centralized CloudWatch logs and metrics. Optional alarms skeleton.
- Per‑environment state isolation and parameterization via SSM Parameter Store.
License: permissive. Contributions welcome.
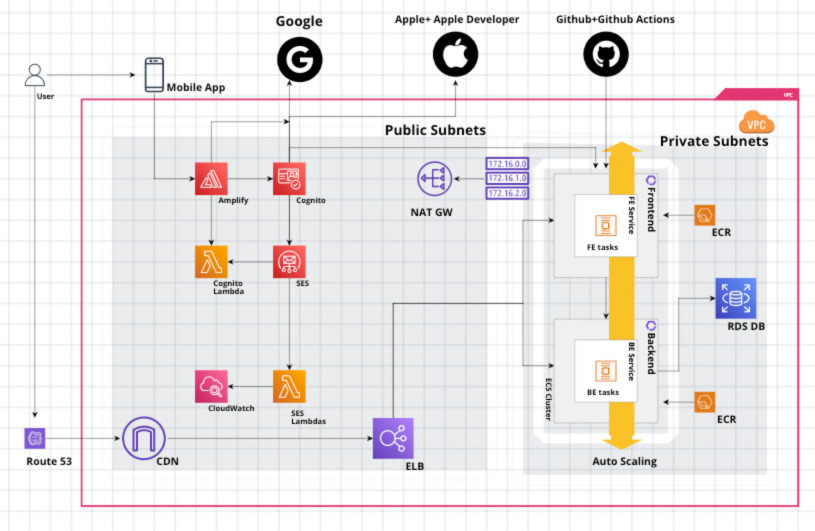
High‑level diagram. Exact module selection varies per project.
Collaborate
I’m iterating in the open. If you want to review the approach, propose changes, or use the modules in your org, send a note.
Quick start
See installation docs for step‑by‑step usage with per‑environment state and variables.
Prefer reproducibility and least privilege. Rotate keys. Enable CloudTrail and Config in your org.